Aruba’s configuration can be a bit confusing at times. The focus of the Aruba Campus Access Fundamentals, Implementing Aruba Campus Access, and ACMP building blocks is to bridge the basic configuration gaps.
Policy Enforcement Firewall
- A firewall policy is a set of rules that examines where the packet is coming from, its destination, and what type of packet it is.
- Firewall policies can allow or deny traffic based on user type or flows.
- After the firewall policy is created, the user role can be created.
- User roles are a set of firewall policies, along with other non-firewall-related items. Examples:
- Quality of Service (QoS)
- Time-Based Access
- User roles are a set of firewall policies, along with other non-firewall-related items. Examples:
- When a session access list is created, it is essentially a firewall policy.
- Firewall policies are stateful.
- Access lists are not stateful.
- Stateful firewall
- Stateful firewalls, also known as stateful inspection firewalls or dynamic packet filtering firewalls, are a type of network security device or software that operates at the network level to monitor and control incoming and outgoing network traffic. They are an evolution of traditional packet-filtering firewalls and provide a higher level of security and sophistication.
- Some of the key characteristics and features of stateful firewalls:
- Stateful Inspection: Stateful firewalls keep track of the state of active connections and the context of the traffic.
- They maintain a state table or stateful connection table that records information about established connections, including source and destination IP addresses, port numbers, and the current state of the connection (e.g., SYN, ESTABLISHED, FIN).
- This stateful approach allows them to make more intelligent decisions about which packets to allow or block.
User Roles
- A user role consists of one or more firewall policies
- The firewall policies consist of one or more firewall rules.
- In Aruba wireless LAN (local area network) controllers, a user role refers to a set of permissions and policies that define what a specific user or group of users can do on the network. These user roles are used to manage and control network access for different types of users, devices, or groups within an organization.
- User roles on Aruba wireless LAN controllers are typically used to enforce security and network access policies. Some common aspects of user roles include:
- Access Permissions: User roles define what resources or areas of the network a user or device can access. This may include access to specific VLANs (Virtual LANs), subnets, or network segments.
- Authentication Requirements: User roles can specify the authentication methods that users must use to access the network. This may include WPA2-PSK (Pre-Shared Key), 802.1X authentication with RADIUS, or other methods.
- Bandwidth and QoS (Quality of Service): User roles can be used to enforce bandwidth limits and prioritize traffic for certain users or devices. This ensures that critical applications receive the necessary network resources.
- Firewall and Security Policies: User roles often include firewall rules that dictate what traffic is allowed or blocked for users in that role. For example, certain user roles may have access to specific services or ports while others are restricted.
- Session Timeout and Idle Timeout: User roles can set session timeout and idle timeout values to automatically disconnect users after a period of inactivity or a maximum session duration.
- Traffic Policing and Shaping: User roles can implement traffic policing and shaping policies to control and manage network traffic.
- Roaming Policies: In a wireless network, user roles can affect how devices roam between access points (APs) and how they are handed off from one AP to another.
- Guest Access: User roles are commonly used to define policies for guest users, providing them with limited access and ensuring they don’t have access to sensitive resources.
- Overall, user roles in Aruba wireless LAN controllers offer network administrators a granular and flexible way to control network access and security. By assigning users or devices to specific roles, administrators can tailor the network experience based on the needs and security requirements of different user groups or types of devices.
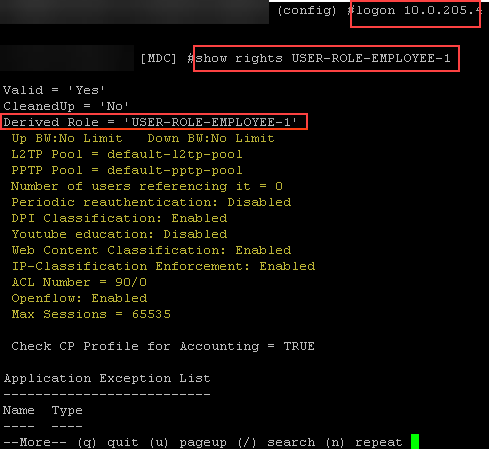
Details about a particular role can be viewed by typing “show rights”
You must be in the correct location to display the user rights based on where it was configured in the hierarchy.
Example:
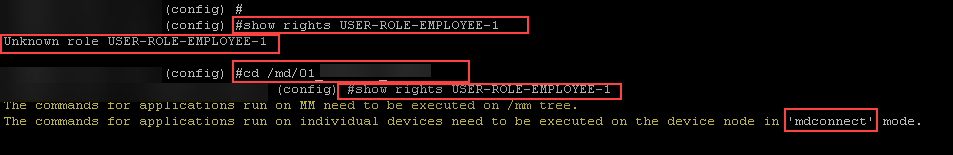
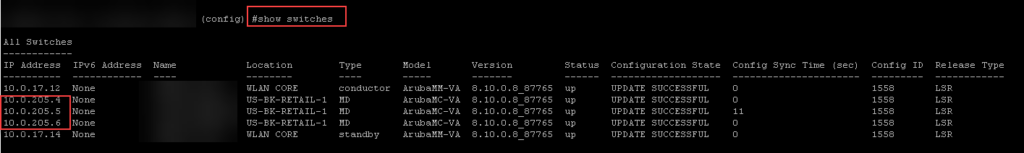
You can directly log into a mobility controller using the “mdconnect” or “logon” command.
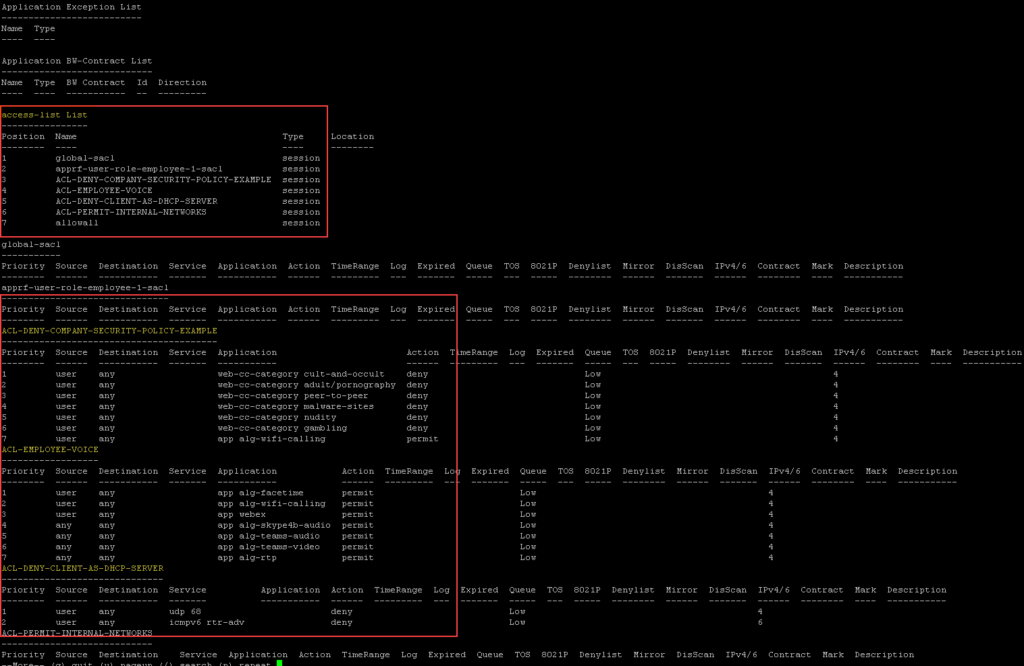
Example Access List
ip access-list extended ACL-STANDARD-EXAMPLE
deny any any host 10.0.0.3
deny any 172.16.0.0 0.0.255.255 192.168.0.0 0.0.0.63
permit any any any
Example Firewall Policy
Permit Real-time applications
ip access-list session ACL-EMPLOYEE-VOICE
user any app alg-facetime permit
user any app alg-wifi-calling permit
user any app webex permit
any any app alg-skype4b-audio permit
any any app alg-teams-audio permit
any any app alg-teams-video permit
any any app alg-rtp permit
!
Deny users from being a DHCP Server
ip access-list session ACL-DENY-CLIENT-AS-DHCP-SERVER
user any udp 68 deny
ipv6 user any icmpv6 rtr-adv deny
Deny Web Categories
ip access-list session ACL-DENY-COMPANY-SECURITY-POLICY-EXAMPLE
user any web-cc-category cult-and-occult deny
user any web-cc-category adult/pornography deny
user any web-cc-category peer-to-peer deny
user any web-cc-category malware-sites deny
user any web-cc-category nudity deny
user any web-cc-category gambling deny
Example User Role Basic Logic
- Create the access list based on the requirements.
- Create the user role
- Associate the access list to the user role.
user-role USER-ROLE-EMPLOYEE-1
access-list session ACL-DENY-COMPANY-SECURITY-POLICY-EXAMPLE
access-list session ACL-EMPLOYEE-VOICE
access-list session ACL-DENY-CLIENT-AS-DHCP-SERVER
access-list session allowallFirewall Policy Structure
- Firewall rules begin with four mandatory parts.
- Source
- Destination
- Service
- Action
If the source, destination, and service values match an inbound packet, then the specified action is executed on the packet.
Source, Destinations, and Aliases
- The source and destination specify where the packets are coming from and where they are going.
- Usually, IP addresses > 172.16.0.1
- Individual hosts > host 172.16.0.254
- Network > 172.16.0.0 255.255.255.0
- An “alias” in the context of an Aruba controller typically refers to a configuration setting that allows you to assign a user-friendly name or label to various network elements, making it easier to manage and identify them.
- Aliases can be applied to various components.
- Predefined system aliases cannot be modified or deleted.
Any
- The “any” alias is a wildcard destination alias and applies to any device, whether it has an IP address or not.
User
- The “user” alias represents the IP address of the user device sending the packet.
- The “user” alias allows you to refer to the user without having the IP address.
- The “user” alias can only reference a device that is in the user table of the controller.
- When used, the IP address of the client device is placed in the firewall rule in place of the word “user.”
- “User” does not have a relation to the user’s identity or username. “user” is just an alias that represents the source IP address of an inbound packet.
- The “user” alias can also be used as a destination in a firewall policy and represents the IP address of “any” device that is in the user table.
- The “user” cannot be used for both the source and destination addresses in a single firewall rule.
Localip
The localip destination alias is used with remote APs. The alias is mapped to the IP address that is assigned to the Ethernet 0 address of the RAP.
Reference commands
(vMM0002-PROD) [mm] (config) #show dpi application
all Show all applications
category Application Category
custom-app Show custom applications
STRING Name of application to show
(vMM0002-PROD) [mm] (config) #show ip access-list
brief Show brief information
STRING Access-list name
(vMM0002-PROD) [mm] (config) #show dpi application category all
Application Categories
----------------------
Name App Category ID Applied
---- --------------- -------
antivirus 1 0
authentication 2 0
behavioral 3 0
cloud-file-storage 4 0
collaboration 5 0