- The hub router is configured with a tunnel source, tunnel mode, and NHRP network ID
- The spokes are configured with a tunnel source, tunnel mode, and NHRP network ID.
- The configuration “ip nhrp nhs” identified the NHRP next-hop server.
- The configuration “ip nhrp map <tunnel IP> <public IP> maps the hub’s tunnel IP to the hub’s PUBLIC IP.
- If the mapping is NOT configured, the spokes will not be able to communicate with the hub router. This mapping is needed because the spokes are configured with a multipoint GRE tunnel.
Configuration and Behavior Between R5 and R1
R5(config-if)#do show run int t2023
!
interface Tunnel2023
ip address 172.16.0.5 255.255.255.0
no ip redirects
ip mtu 1476
ip nhrp network-id 523
ip tcp adjust-mss 1436
tunnel source Ethernet0/0.100
tunnel mode gre multipoint
end
R1#show run int t2023
interface Tunnel2023
ip address 172.16.0.1 255.255.255.0
no ip redirects
ip nhrp map 172.16.0.5 169.1.100.5
ip nhrp network-id 123
ip nhrp nhs 172.16.0.5
tunnel source 169.1.100.1
tunnel mode gre multipoint
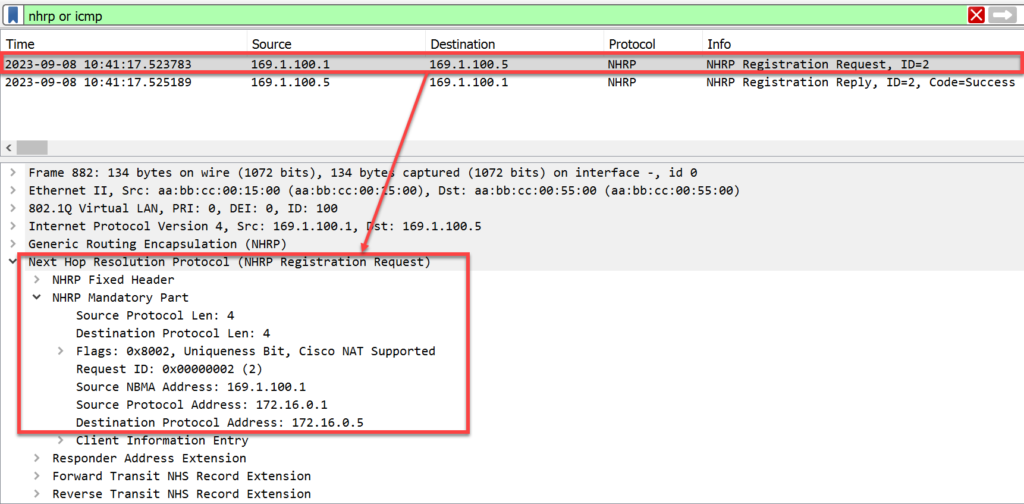
endR1 (Spoke) sends an NHRP Request to R5 (Hub)
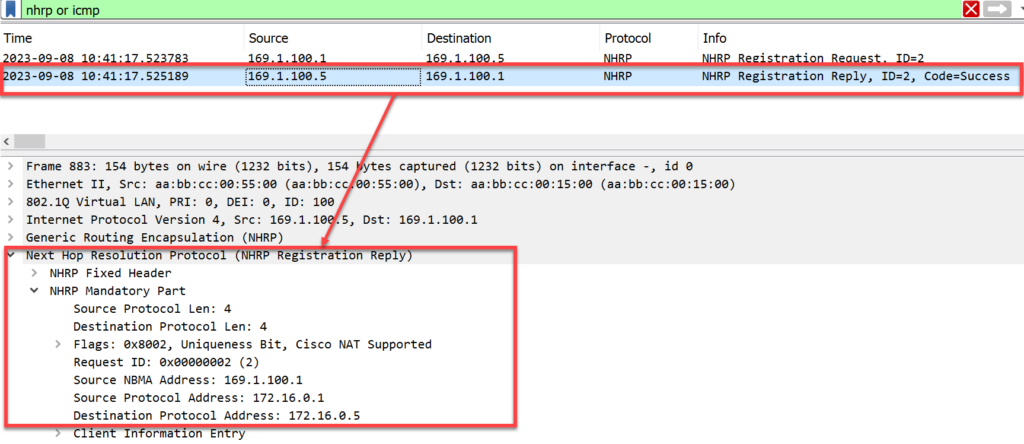
R5 (Hub) Responds with a Registration Reply Success Message
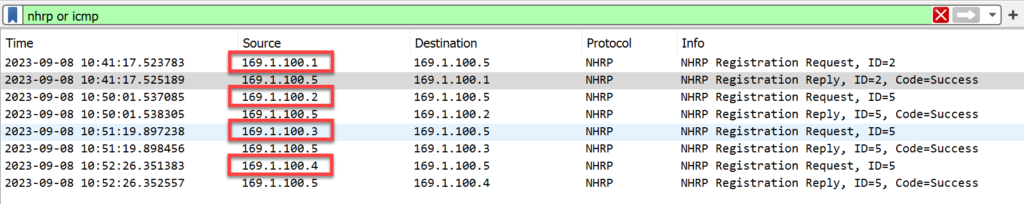
The exchange described above should be identical for R2, R3, and R4
R2
interface Tunnel2023
ip address 172.16.0.2 255.255.255.0
no ip redirects
ip nhrp map 172.16.0.5 169.1.100.5
ip nhrp network-id 223
ip nhrp nhs 172.16.0.5
tunnel source 169.1.100.2
tunnel mode gre multipoint
endR3
interface Tunnel2023
ip address 172.16.0.3 255.255.255.0
no ip redirects
ip nhrp map 172.16.0.5 169.1.100.5
ip nhrp network-id 323
ip nhrp nhs 172.16.0.5
tunnel source 169.1.100.3
tunnel mode gre multipoint
endR4
interface Tunnel2023
ip address 172.16.0.4 255.255.255.0
no ip redirects
ip nhrp map 172.16.0.5 169.1.100.5
ip nhrp network-id 423
ip nhrp nhs 172.16.0.5
tunnel source 169.1.100.4
tunnel mode gre multipoint
endWireshark verification
R5#show ip nhrp
172.16.0.1/32 via 172.16.0.1
Tunnel2023 created 00:13:22, expire 01:46:37
Type: dynamic, Flags: unique registered used nhop
NBMA address: 169.1.100.1
172.16.0.2/32 via 172.16.0.2
Tunnel2023 created 00:04:38, expire 01:55:21
Type: dynamic, Flags: unique registered used nhop
NBMA address: 169.1.100.2
172.16.0.3/32 via 172.16.0.3
Tunnel2023 created 00:03:20, expire 01:56:39
Type: dynamic, Flags: unique registered used nhop
NBMA address: 169.1.100.3
172.16.0.4/32 via 172.16.0.4
Tunnel2023 created 00:02:14, expire 01:57:45
Type: dynamic, Flags: unique registered used nhop R5#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
T1 - Route Installed, T2 - Nexthop-override
C - CTS Capable
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel2023, IPv4 NHRP Details
Type:Hub, NHRP Peers:4,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 169.1.100.1 172.16.0.1 UP 00:13:20 D
1 169.1.100.2 172.16.0.2 UP 00:04:36 D
1 169.1.100.3 172.16.0.3 UP 00:03:18 D
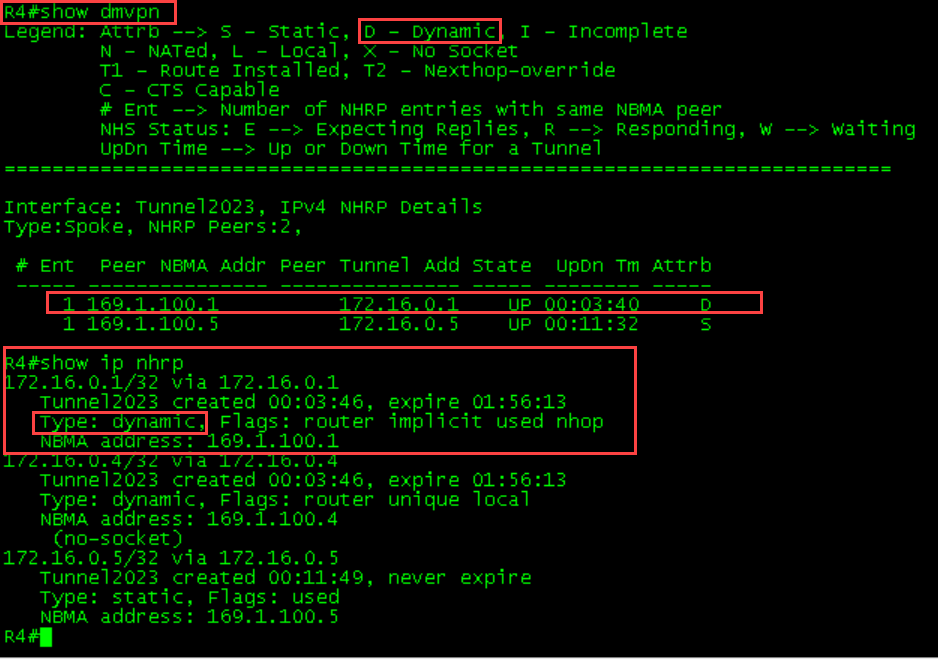
1 169.1.100.4 172.16.0.4 UP 00:02:11 DR1-R4 Initial Tables
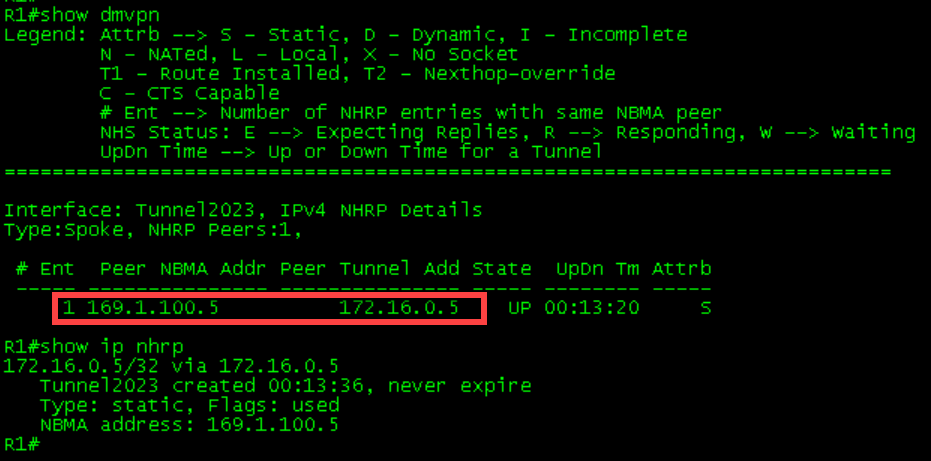
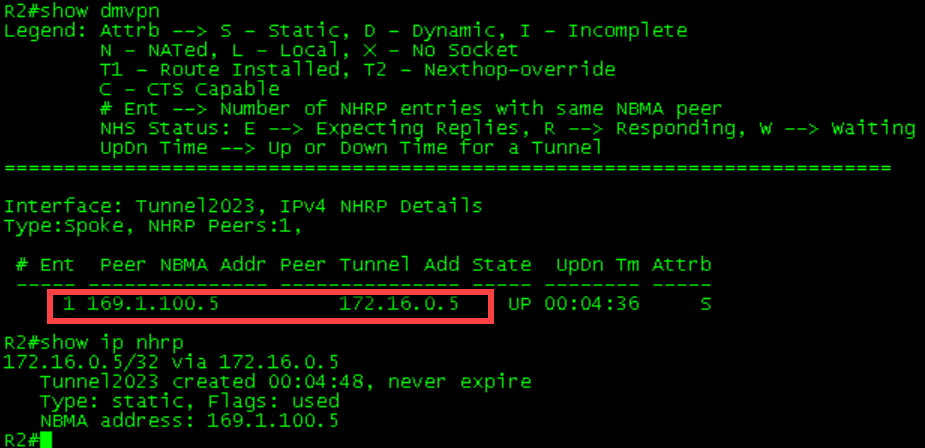
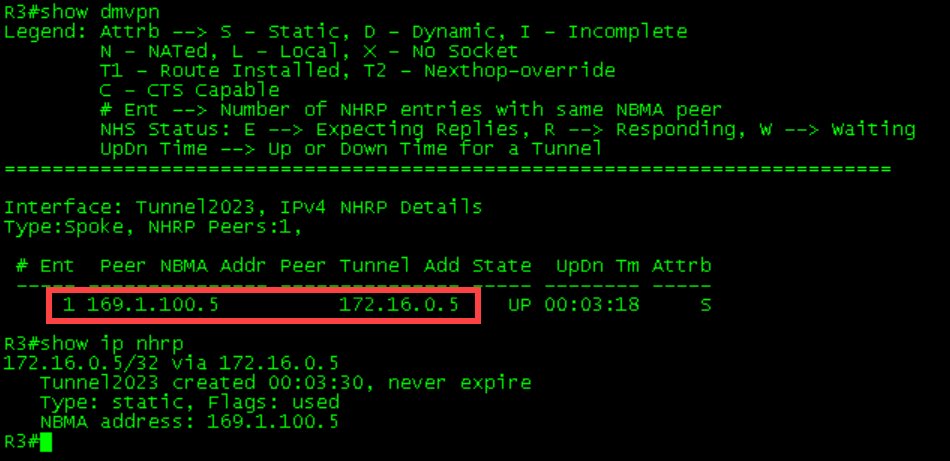
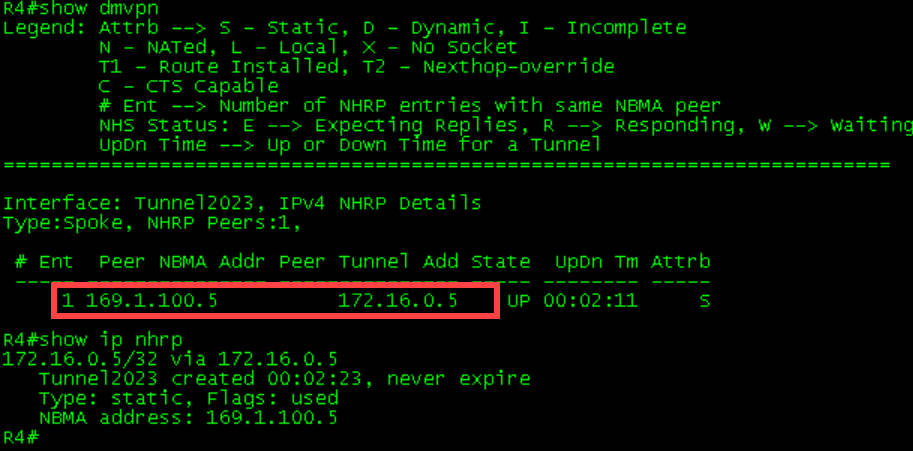
Verifying Traffic Flow
R1 ping to R4
R1
R1#ping 172.16.0.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.0.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/4/7 ms
R1#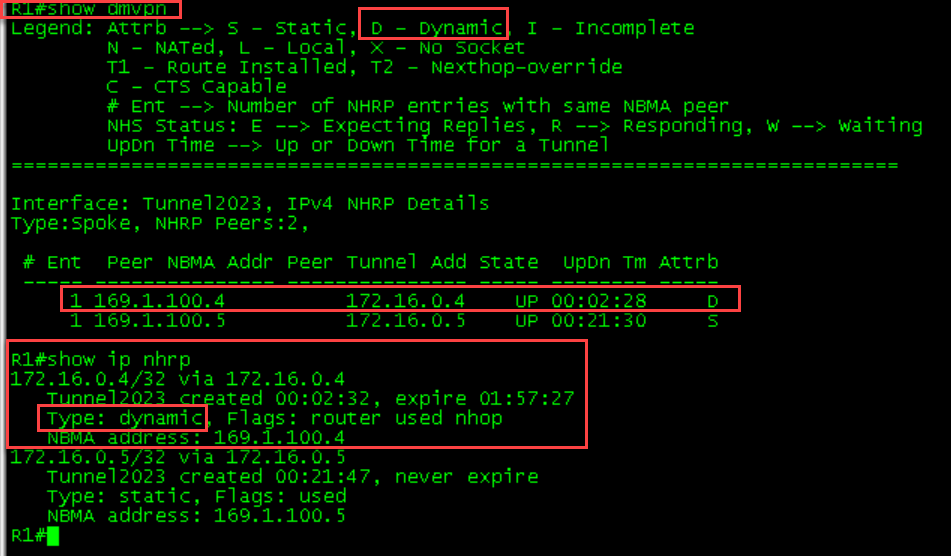
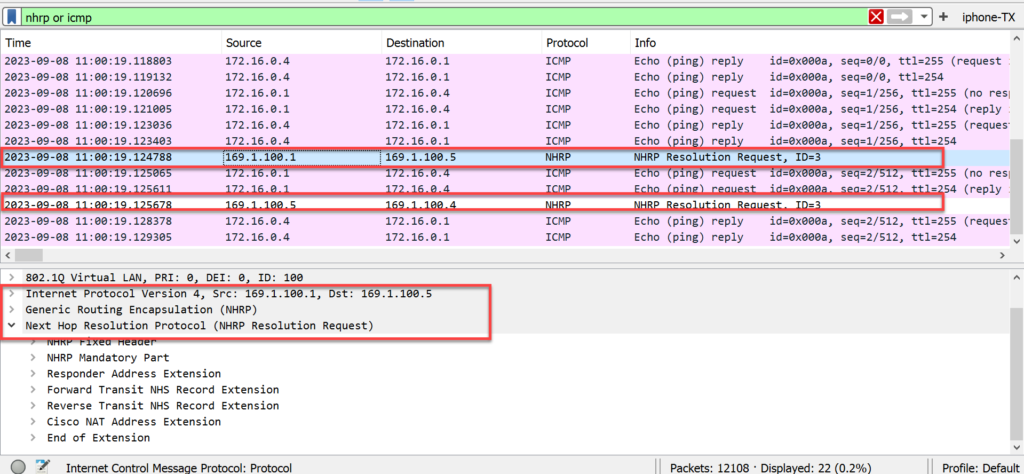
Wireshark shows the resolution request between the Hub and Spoke
R1 traceroute to R3
R1 did not have a dynamic mapping for the IP address for R3. The initial traceroute went through R5 (Hub). This is the correct operation for building the communication between the spokes.
The second trace route went directly to R3 once the dynamic mapping was created.
R1#traceroute 172.16.0.3
Type escape sequence to abort.
Tracing the route to 172.16.0.3
VRF info: (vrf in name/id, vrf out name/id)
1 172.16.0.5 3 msec 2 msec 2 msec
2 172.16.0.3 4 msec * 7 msec
R1#
R1#traceroute 172.16.0.3
Type escape sequence to abort.
Tracing the route to 172.16.0.3
VRF info: (vrf in name/id, vrf out name/id)
1 172.16.0.3 7 msec * 2 msec
R1#Wireshark Verification
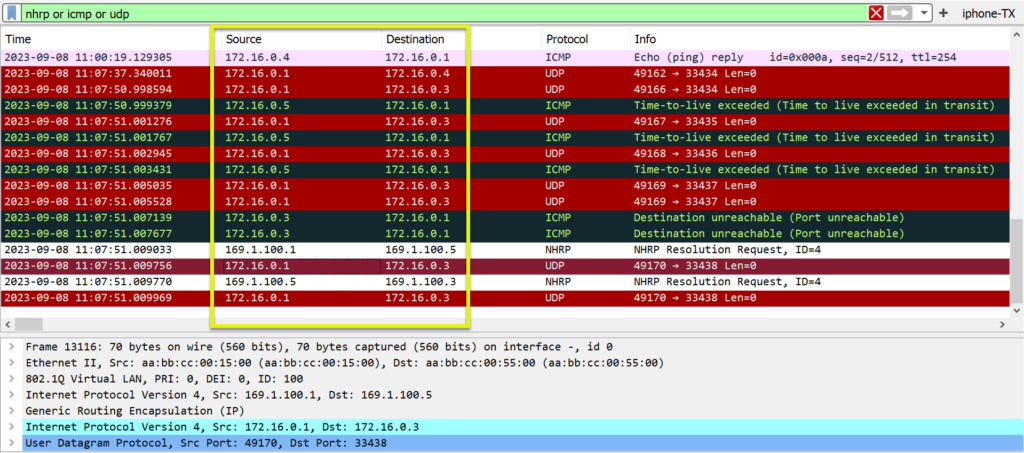
Verification of updated mapping tables
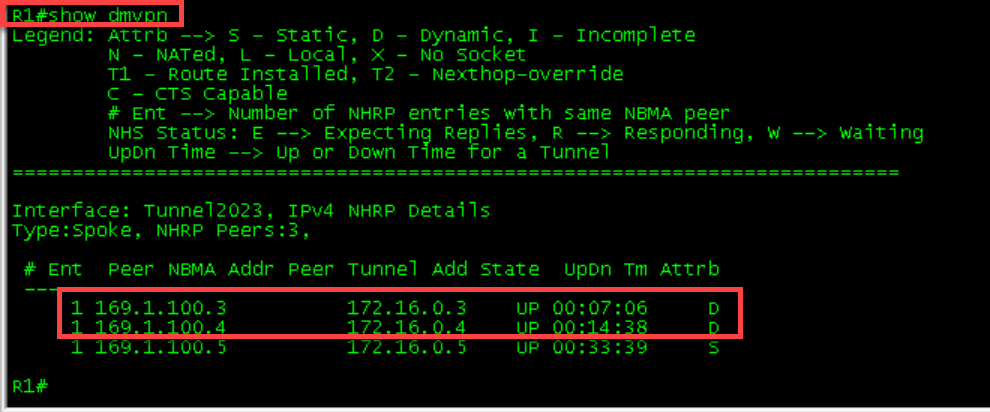
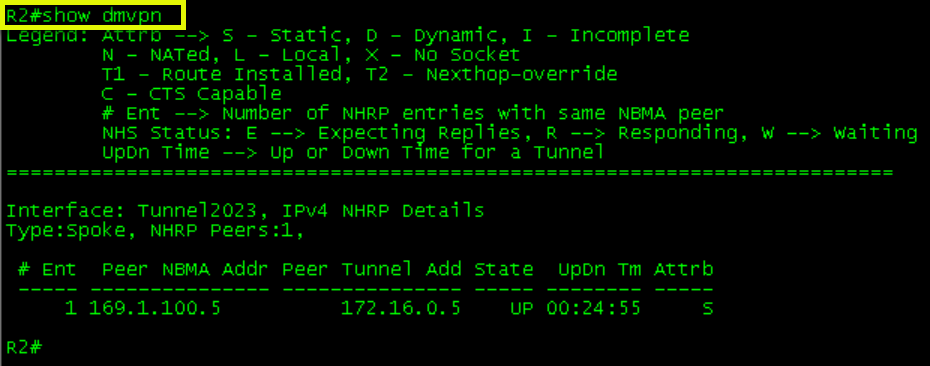
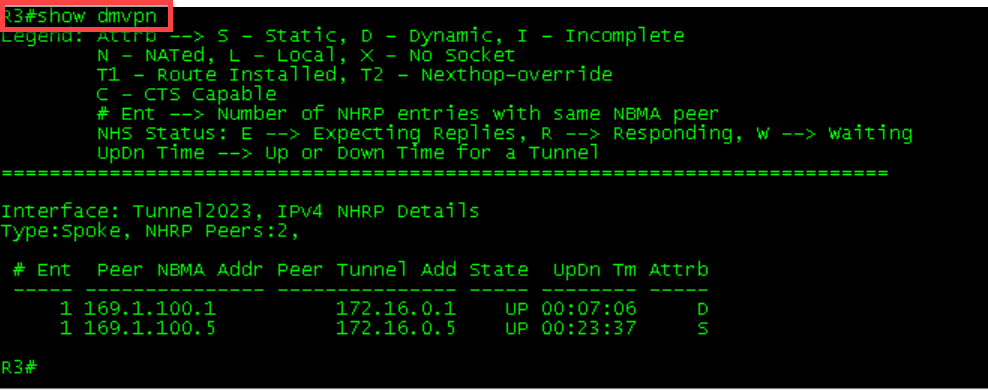
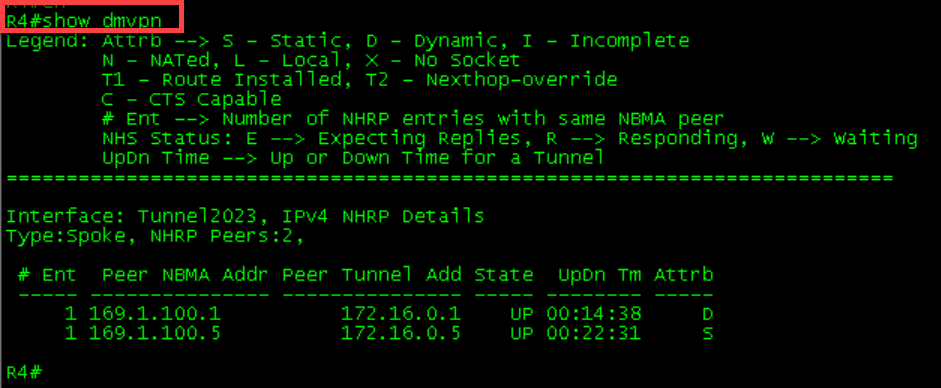
R2’s table was not updated because no other spoke has tried communicating with it. Running a ping from all devices will allow the dynamic mapping to occur.
R1#tclsh
R1(tcl)#foreach VAR {
+>(tcl)# 172.16.0.2
+>(tcl)#} { puts [exec "ping $VAR"] }
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.0.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/3/4 ms
R3#tclsh
R3(tcl)#foreach VAR {
+>(tcl)# 172.16.0.2
+>(tcl)#} { puts [exec "ping $VAR"] }
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.0.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 3/4/6 ms
R3(tcl)#
R3(tcl)#tclquit
R4#tclsh
R4(tcl)#foreach VAR {
+>(tcl)# 172.16.0.2
+>(tcl)#} { puts [exec "ping $VAR"] }
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.0.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 3/5/9 msR2’s updated mappings
R2#show dmvpn
Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete
N - NATed, L - Local, X - No Socket
T1 - Route Installed, T2 - Nexthop-override
C - CTS Capable
# Ent --> Number of NHRP entries with same NBMA peer
NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting
UpDn Time --> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel2023, IPv4 NHRP Details
Type:Spoke, NHRP Peers:4,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 169.1.100.1 172.16.0.1 UP 00:00:09 D
1 169.1.100.3 172.16.0.3 UP 00:00:07 D
1 169.1.100.4 172.16.0.4 UP 00:00:05 D
1 169.1.100.5 172.16.0.5 UP 00:31:06 S
R2#show ip nhrp
172.16.0.1/32 via 172.16.0.1
Tunnel2023 created 00:03:06, expire 01:56:53
Type: dynamic, Flags: router implicit used nhop
NBMA address: 169.1.100.1
172.16.0.2/32 via 172.16.0.2
Tunnel2023 created 00:03:06, expire 01:56:57
Type: dynamic, Flags: router unique local
NBMA address: 169.1.100.2
(no-socket)
172.16.0.3/32 via 172.16.0.3
Tunnel2023 created 00:03:04, expire 01:56:55
Type: dynamic, Flags: router nhop
NBMA address: 169.1.100.3
172.16.0.4/32 via 172.16.0.4
Tunnel2023 created 00:03:02, expire 01:56:57
Type: dynamic, Flags: router used nhop
NBMA address: 169.1.100.4
172.16.0.5/32 via 172.16.0.5
Tunnel2023 created 00:34:12, never expire
Type: static, Flags: used
NBMA address: 169.1.100.5
R2#