WLAN configured for WPA3 SAE with backward compatibility

Confirmation via airodump-ng

Confirmation via Wireshark

The client connected after going through the normal four-way handshake process

Client connected


Create a rouge access point that will broadcast an RSN IE of WPA2. The PSK is incorrect.
Verify the wireless interfaces

Contents of the script

Start airodump-ng before running the fake AP.

Start fake AP

Clients are already trying to auth against the fake AP

The fake AP does not know the correct PSK, but the client and AP will exchange a few frames. The four-way hand-shake was captured.

Verify frame exchange and beacon frames. We can see that the auth key management now displays PSK with AES.


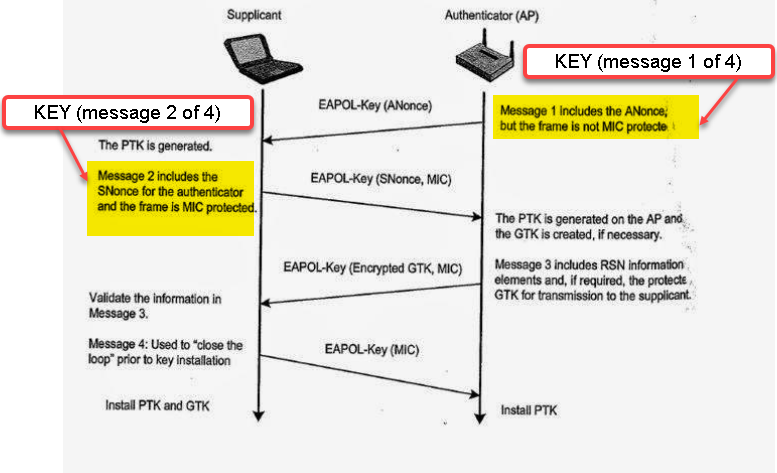
- The transaction between the AP and client CAN NOT move past key 2 as the AP does not have the correct PSK defined.

Attempt to retrieve the PSK via a dictionary attack.
