This lab will demonstrate how to configure a simple web passthrough on the IOS XE 9800 Controller
AireOS web passthrough settings



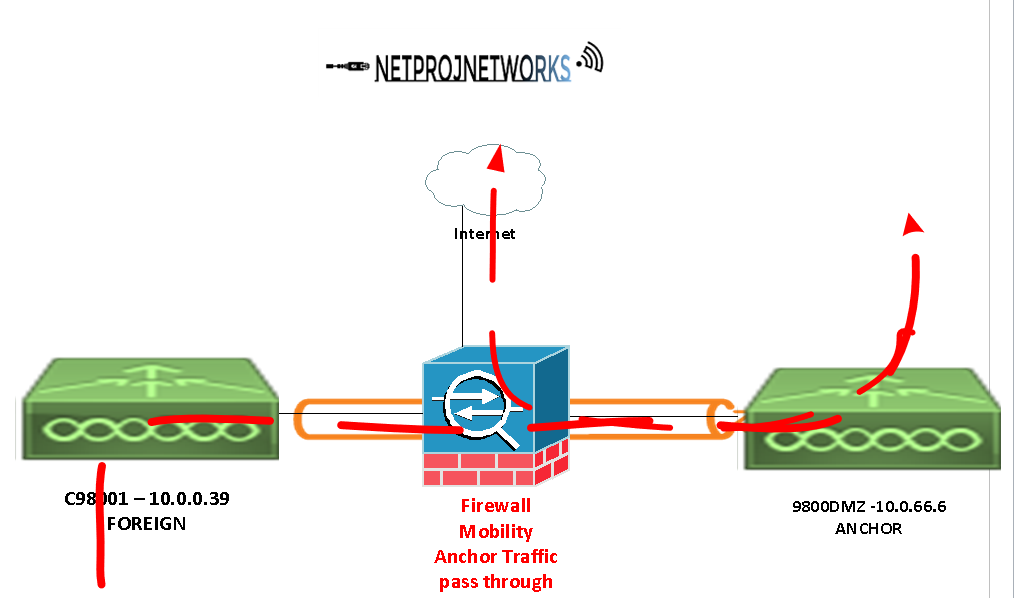
Configure the IOS XE 9800 Controllers – as usual the guest users will be dropped off in the DMZ
Both WLCs MUST have identical configurations
First verify that the mobility tunnel is in an UP state on both the foreign and the anchor
FOREIGN

ANCHOR

We see that both devices see each others mobility tunnel as up
Items that should be configured
Custom web page – the sample web consent package can be downloaded from Cisco.com. Once the file(s) have been downloaded and edited they must be renamed in the following format web_auth_<filename>. Use the standard copy feature from ftp,scp etc to copy the file to the bootflash.

Parameter map(s)
Foreign

Anchor

Foreign – Create the policy profile



Policy on the Anchor
The name of the policy and the settings on both the Anchor and Foreign must MATCH 100% with the exception of the VLAN and mobility anchor



My best practice is to test basic connectivity first. This means that i do not apply any type of MAC filtering or AAA polices. Once i verify that the client device can obtain and IP i then apply the AAA polices.
In my testing the custom web page is “housed” on the Anchor controller not on the Foreign. A public certificate is also required on the DMZ Anchor.
WLAN Config – As usual the configurations must be identical
Foreign and Anchor


Time to test
web passthrough is meant to be a simple guest solution. Authentication is NOT in use, the user either agree or reject the user acceptance page. That’s it. The controller is NOT tied to AAA, it host the custom web page and intercepts the initial HTTP request and presents the consent/aup page to the user.
User does not have access to the network and is NOT on the WLC


A quick way to deauth a user is from the CLI. Type the following command for each MAC address you want to deauth.


Connect laptop to guest wireless
The user has a VALID IP address from the DMZ. Also note the state of the user. A user than can pass traffic through the controller is in the run state. Although the user is in the run state notice that the “auth method” is “web auth”. At this time the controller should present the custom web portal to the user.

verify client state

Again, with web passthrough captive portal the user is not required to enter a username and password. They are presented with an accept button.
Once the user click the accept button they will be allowed onto the network

At this time the user should also be redirected to the specified web portal. In this case i defined www.disney.com
